A team of astronomers has made a surprising discovery using the U.S. National Science Foundation Green Bank Telescope (NSF GBT): eleven fast-moving clouds of cold, neutral hydrogen gas—akin to “ice cubes”—surviving deep inside the Fermi Bubbles.
Recent News
ALMA Reveals Stunning Details of Infant Galaxies in the Early Universe
The [CII] Resolved ISM in STar-forming galaxies with ALMA (CRISTAL survey) peered back to when the Universe was only about one billion years old – a mere toddler in cosmic terms. These observations are helping scientists understand how galaxies formed and evolved from primordial gas clouds into the organized structures we see today.
NSF NRAO Leads Critical Spectrum Studies to Safeguard Radio Astronomy
The U.S. National Science Foundation National Radio Astronomy Observatory (NSF NRAO) has received funding to expand its study of an invisible—and crucial—scientific and technological resource: the radio spectrum.
Industrial Cybersecurity: A Culture Change
The following is an article from UPDATE, the official publication of Utah Petroleum Association, Issue 4 2020.
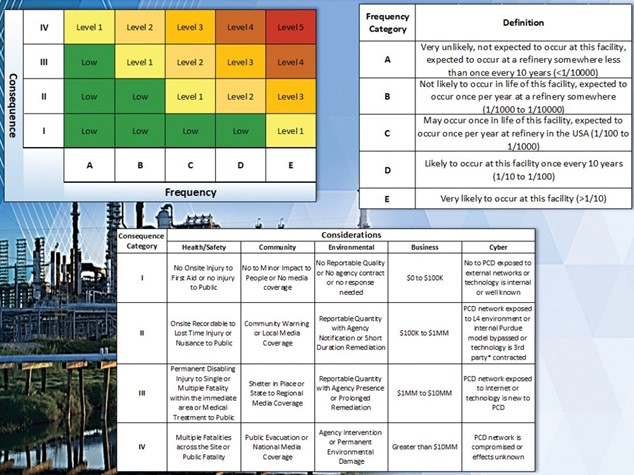
To highlight a few areas of key importance, organizations must set the cyber- security standards they will follow. For example, government agencies closely follow the standards of the National Institute of Standards and Technology (NIST); for OT, that standard would be NIST SP-800-82. Not all the recommendations may be required, as each organization’s infrastructure is different, hence why risk assessments are extremely important. In addition to NIST, other standards include International Organization for Standardization (ISO/IEC), North American Electric Reliability Corporation (NERC-CIP), American National Standards institute or International Society for Automations (ANSI/ISA), and/or Center for Internet Security (CIS). These standards, along with the associated risk characteristics of an organization’s infrastructure, will create the initial draft of policies and procedures. These initial, steps coupled with employee training, are key in creating a strong base for cybersecurity initiatives.
The threats of cybersecurity to OT/ICS environments have expanded drastically across all sectors of industry. Malicious actors have leveraged insider threats, ransomware, networking pivoting, policy violations, and compromising third party relations to gain a foot hold into OT and critical infrastructure networks. Examples include Stuxnet, TRISIS, Shamoon (1-3), and WannaCry. Specifically, in the oil and gas industry, several entities are gaining sophistication in their targeted attacks, including Xenotime, Magnallium, Dymalloy, Chrysene, Hexane, and nation-state or quasi-government actors.
The first step towards securing infrastructure is a culture change that all organizations and their employees need to adopt; that is, making cybersecurity a new priority. Cybersecurity threats are growing, and organizations must respond to protect its people, imagine, community, and the security of our nation.

Terry Horn, Director of Operation Technology, Associated Universities Inc. Woodstar Labs Cybersecurity
Terry Horn joined AUI as a leader in cybersecurity operational technology. He focuses on business development, strategic technologies in industrial control systems (ICS), cybersecurity initiatives, and conducting hands-on assessments for clients and partners within the ICS and operational technology cybersecurity domain.
Related Publications/Contributions:
Author: There is More to Simulation Data, White Paper, Booz Allen, FEB-2016. | Fishing Through SCADA, White Paper, Booz Allen, MAR-2016. | Obtaining SCADA Simulation Data, White Paper, Booz Allen, MAR-2016. | Going Wireless within SCADA, White Paper, Booz Allen, APR-2016. | Manufacturing Control Systems, White Paper, Booz Allen, SEP-2016
Contributor: Cybersecurity Risk Steering Committee; Northeast Big Data Innovation Hub, NYU, Columbia University Control System Cybersecurity Association International
Recent News
Galactic Mystery: How “Ice Cubes” Survive in the Milky Way’s Blazing Bubbles
A team of astronomers has made a surprising discovery using the U.S. National Science Foundation Green Bank Telescope (NSF GBT): eleven fast-moving clouds of cold, neutral hydrogen gas—akin to “ice cubes”—surviving deep inside the Fermi Bubbles.
ALMA Reveals Stunning Details of Infant Galaxies in the Early Universe
The [CII] Resolved ISM in STar-forming galaxies with ALMA (CRISTAL survey) peered back to when the Universe was only about one billion years old – a mere toddler in cosmic terms. These observations are helping scientists understand how galaxies formed and evolved from primordial gas clouds into the organized structures we see today.
NSF NRAO Leads Critical Spectrum Studies to Safeguard Radio Astronomy
The U.S. National Science Foundation National Radio Astronomy Observatory (NSF NRAO) has received funding to expand its study of an invisible—and crucial—scientific and technological resource: the radio spectrum.
