A new study connects the black hole’s famous ring of light to a compact region that marks the likely base of the jet, bringing scientists closer to understanding how black holes power some of the brightest beacons in the universe.
Recent News
Magnetic Superhighways Discovered in a Starburst Galaxy’s Winds
Using the Atacama Large Millimeter/submillimeter Array (ALMA), an international team of astronomers has mapped a magnetic highway driving a powerful galactic wind into the nearby galaxy merger of Arp 220, revealing for the first time that its fast, molecular outflows are strongly magnetized and likely helping to drive metals, dust, and cosmic rays into the space around the galaxy.
Making Scientific Breakthroughs Possible in 2025
2025 was an incredibly productive year for AUI, marked by significant advances across astronomy, energy, advanced therapeutics, and STEM education and workforce development.
Industrial Cybersecurity: A Culture Change
The following is an article from UPDATE, the official publication of Utah Petroleum Association, Issue 4 2020.
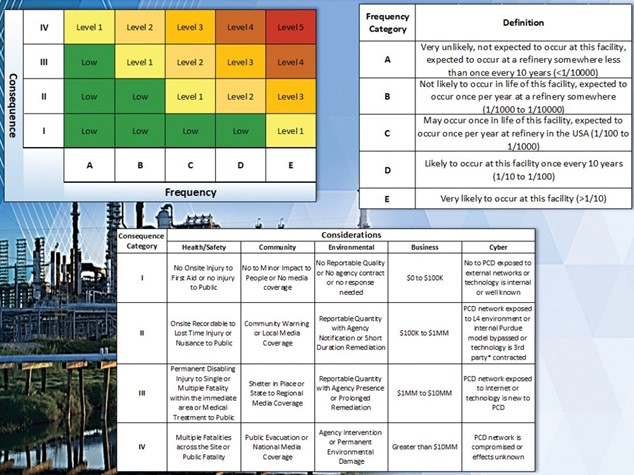
To highlight a few areas of key importance, organizations must set the cyber- security standards they will follow. For example, government agencies closely follow the standards of the National Institute of Standards and Technology (NIST); for OT, that standard would be NIST SP-800-82. Not all the recommendations may be required, as each organization’s infrastructure is different, hence why risk assessments are extremely important. In addition to NIST, other standards include International Organization for Standardization (ISO/IEC), North American Electric Reliability Corporation (NERC-CIP), American National Standards institute or International Society for Automations (ANSI/ISA), and/or Center for Internet Security (CIS). These standards, along with the associated risk characteristics of an organization’s infrastructure, will create the initial draft of policies and procedures. These initial, steps coupled with employee training, are key in creating a strong base for cybersecurity initiatives.
The threats of cybersecurity to OT/ICS environments have expanded drastically across all sectors of industry. Malicious actors have leveraged insider threats, ransomware, networking pivoting, policy violations, and compromising third party relations to gain a foot hold into OT and critical infrastructure networks. Examples include Stuxnet, TRISIS, Shamoon (1-3), and WannaCry. Specifically, in the oil and gas industry, several entities are gaining sophistication in their targeted attacks, including Xenotime, Magnallium, Dymalloy, Chrysene, Hexane, and nation-state or quasi-government actors.
The first step towards securing infrastructure is a culture change that all organizations and their employees need to adopt; that is, making cybersecurity a new priority. Cybersecurity threats are growing, and organizations must respond to protect its people, imagine, community, and the security of our nation.

Terry Horn, Director of Operation Technology, Associated Universities Inc. Woodstar Labs Cybersecurity
Terry Horn joined AUI as a leader in cybersecurity operational technology. He focuses on business development, strategic technologies in industrial control systems (ICS), cybersecurity initiatives, and conducting hands-on assessments for clients and partners within the ICS and operational technology cybersecurity domain.
Related Publications/Contributions:
Author: There is More to Simulation Data, White Paper, Booz Allen, FEB-2016. | Fishing Through SCADA, White Paper, Booz Allen, MAR-2016. | Obtaining SCADA Simulation Data, White Paper, Booz Allen, MAR-2016. | Going Wireless within SCADA, White Paper, Booz Allen, APR-2016. | Manufacturing Control Systems, White Paper, Booz Allen, SEP-2016
Contributor: Cybersecurity Risk Steering Committee; Northeast Big Data Innovation Hub, NYU, Columbia University Control System Cybersecurity Association International
Recent News
New Event Horizon Telescope Results Trace M87 Jet Back to Its Black Hole
A new study connects the black hole’s famous ring of light to a compact region that marks the likely base of the jet, bringing scientists closer to understanding how black holes power some of the brightest beacons in the universe.
Magnetic Superhighways Discovered in a Starburst Galaxy’s Winds
Using the Atacama Large Millimeter/submillimeter Array (ALMA), an international team of astronomers has mapped a magnetic highway driving a powerful galactic wind into the nearby galaxy merger of Arp 220, revealing for the first time that its fast, molecular outflows are strongly magnetized and likely helping to drive metals, dust, and cosmic rays into the space around the galaxy.
Making Scientific Breakthroughs Possible in 2025
2025 was an incredibly productive year for AUI, marked by significant advances across astronomy, energy, advanced therapeutics, and STEM education and workforce development.
